
![]()
|
|
Software that installs on top of MS Windows NT 4.0 Terminal Server Edition (TSE) and extends many of its capabilities. |
|
|
Metaframe incorporates the ICA protocol, which allows for a much wider range of client type and protocol connectivity. |
|
|
Metaframe also allows for better enterprise level management, scalability and performance through many of its features. |
|
|
TSE with its proprietary RDP presentation protocol is limited to running over TCP/IP and TCP/IP over RAS. |
|
|
Metaframe’s ICA presentation protocol runs over TCP/IP, IPX/SPX, NetBIOS, RAS, Dial-in Asynchronous. |
|
|
Allows for the direct serial connection of keyboard(s) and monitor(s) to a single Metaframe server configured with a special VGA multi-port video adapter. |
|
|
A good option for graphically intense applications such as CAD. |
|
|
A very nice feature that can automatically map client side printers and local drives, and allows for client COM and LPT port redirection to the user’s Metaframe session. |
|
|
Also provides the capability of Audio mapping and Clipboard mapping. |
|
|
The ability to “look over a user’s shoulder” while they are logged on. You can see everything the user sees and therefore this feature is very good for technical support issues. |
|
|
Shadowing requires ICA client software (even when running from the server) and an additional client license is consumed while in use. |
|
|
Provides the ability for users to use only applications rather than connecting to the full desktop. This feature goes hand-in-hand with program neighborhood and Web application access. |
|
|
Metaframe installs 15 local anonymous user accounts that can be used in situations where secure access is unnecessary. Very useful feature for Web application access. |
|
|
Feature that provides for much better application availability via published applications. |
|
|
Applications can be published across 2 or more servers. Servers can fail or be taken down for maintenance and the application will still be available. |
|
|
Not to be confused with fault tolerance! |
|
|
Another application publishing feature that allows servers to be grouped together as a single entity. |
|
|
Primarily used with program neighborhood on the client side, which dynamically allows applications to be “pushed” out to users based on domain access permissions. |
|
|
Citrix client software for Win32 platforms that allows for a more dynamic application environment. |
|
|
Non Win32 platforms can benefit from program neighborhood via the pass-through technology of Metaframe. |
|
|
Client side bitmap caching that minimizes bandwidth usage and improves end user experience |
|
|
40, 56 and 128 bit encryption for North American customers and 40 bit encryption for International users allows for better security at the cost of additional SecureICA licensing |
|
|
Large scale enterprises distributing applications over a WAN can greatly improve their management and scalability with Metaframe’s many features. Smaller businesses can make use of ICA and its wide range of client types and protocols to save money by retaining existing PCs, DOS terminals and MACs. |
|
|
Requires a clean system, or can be installed on top of NT 3.51, 4.0, Winframe 1.6, 1.7 or 1.8. |
|
|
Local security will be preserved; however, applications will need to be reinstalled. |
|
|
Hardware compatible with MS HCL for NT Server 4.0. |
|
|
Requires Pentium processor, VGA resolution or higher, 300Meg of disk space, CD ROM, 32Meg RAM + 4-12Meg RAM/user, NIC and mouse. |
|
|
User Manager for Domains (UMFD) is the tool that configures properties for single or multiple users. |
|
|
You must use the UFMD that ships with TSE in order to configure TSE-specific properties. |
|
|
The user Config button displays options for individual user connections. A check box allows or disallows user to log on to TSE. If checked, you can configure user timeout settings, client device settings, an initial program to run at logon, and various connection and shadowing options. |
|
|
The Profile button allows you to specify settings for normal NT profiles as well as TSE profiles. The terminal server profile path and the terminal server home directory path are useful for segregating NT from TSE profiles. |
|
|
Start by either going to the “Add/Remove Programs” applet in the Control Panel or by going to a command prompt and typing CHANGE USER /INSTALL. |
|
|
Install the application as you would normally then when finished, type CHANGE USER /EXECUTE at the command prompt. |
|
|
The command prompt method enables and disables ini file and registry mapping in order to propagate user settings in the multi-user environment. |
|
|
Requires a server with TSE installed + at least 30 MB of additional disk space and all necessary network protocols previously installed. |
|
|
Metaframe is compatible with MS HCL for NT Server 4.0. |
|
|
Factors influencing server sizing and protocol choices include the number of users per server, types and usage of applications, and locations of users relative to the server (LAN, WAN, dial-up, RAS, Web or VPN). |
|
|
Performance monitor used with load testing can give a good picture of how this all works together prior to production deployment. |
|
|
Locate the 21-character serial number that begins with 3 letters. You can usually find this serial number on the box or the CD jewel case. |
|
|
Enter the serial number into the Citrix licensing utility or during initial Metaframe setup. (Note: For this test, the license will last for 30 days inactivated—real life, it lasts for 35 days!) |
|
|
Obtain an activation code from Citrix via the Citrix Activation Wizard over the Internet, by modem, by telephone, or by Fax. Fastest method is via the wizard. |
|
|
Enter the activation code into the Citrix licensing utility for the license. |
|
|
TCP/IP will always be present in a TSE installation. In addition you need IPX/ SPX for Novell support, NetBIOS/NetBEUI for legacy DOS and Windows networks and Asynchronous modems. |
|
|
If NetBIOS is installed on a TSE server, NWLink and NetBEUI will be installed during Metaframe installation. |
|
|
When Metaframe installs, ICA listener ports will automatically be set up for each protocol type installed previously on TSE. |
|
|
Workstations requiring connection to a Metaframe server need to be running at least one of the protocols. |
|
|
Mac and UNIX clients require a special Metaframe client and additional support on the server. |
|
|
ICA traffic by default is passed through TCP port 1494. ICA browser traffic by default is passed through UDP port 1604. |
|
|
If server has RAS ports configured, they CANNOT be used for Async connections. |
|
|
Async connections can be configured during the Metaframe install or later using the Citrix Connection Configuration (CCC) utility. |
|
|
Citrix recommends using high-speed serial ports or intelligent multi-port hardware to ease the processing burden of the server. |
|
|
During configuration, the wizard allows you to install a modem if necessary or selects a previously installed modem. |
|
|
Only TAPI compliant modems can be used. |
|
|
This is most useful when you purposely redirect client drives at logon. |
|
|
This process is best done during initial setup; doing it later can cause problems with application and system paths. |
|
|
The benefit of server drive letter re-assignment is to minimize user confusion. They see their own local PC drives as C:, D:, etc; server drives are set to M:, N:, etc. |
|
|
Frame head, reliable, encryption, compression, command, command data, and frame trail can all be present in an ICA packet. |
|
|
Only command is always present |
|
|
Win16 (Win3.1 Enhanced mode, and 3.11) running NetBIOS, IPX/SPX, TCP/IP, and Async. |
|
|
Win32 (9x, NT 3.51 and up, MF/WF) running the same protocol stacks as Win16. |
|
|
WinCE (2.0 and up) running only TCP/IP, client s/w only available from OEM vendors. |
|
|
Web (ALE) client for IE and Netscape. Only TCP/IP connections allowed. |
|
|
DOS16 (3.3 and up) running same protocol stacks as Win16. |
|
|
DOS32 (4 and up) running same protocol stacks as Win16. |
|
|
UNIX (DEC3.2, HPUX10.x, AIX4.1.4, RedHat 5.1, SCO 2.1, SGI IRIX 6.2, Solaris 2.5.1 SPARC, 2.6 x86, SunOS 4.1.4. Only TCP/IP connections allowed. |
|
|
Mac (7.5.3 and up) running only TCP/IP. |
|
|
Java (JDK1.0 and up) running only TCP/IP. |
|
|
A unique workstation name, destination directory and destination folder are required to install client software for all client types. |
|
|
Allows for client server communication over an RC5 encrypted link. |
|
|
It is a separately purchased option pack from Citrix. |
|
|
Two versions are available: North American (40, 56 and 128 bit) and International (40 bit only). |
|
|
Secure ICA software must be installed on both client and server. Client must have at least the level of encryption that the server has in order to connect. |
|
|
Encryption levels can be set in UMFD for individual users and the CCC utility for all users for a given connection. |
|
|
Win32, Win16, Web and DOS clients can utilize SecureICA. |
|
|
Application Set Manager contains icons used to manage and connect to application sets. |
|
|
Options that can be set include: connection type, description, application set, server location, sound, window color, and window size. |
|
|
The find new application set wizard allows user to connect to remote server farms. |
|
|
Custom ICA connection wizard allows user to set up custom connections to published applications. |
|
|
Add ICA connection and Find new application set wizards by default configure compressed data stream, low speed connections to bitmap cache, no queuing of mouse movements and keyboard strokes, set encryption to the highest available on the client. |
|
|
All applications and resources (server-based and local) on the client appear as if they are all running locally. |
|
|
Client drive redirection, client printer mapping, clipboard mapping, serial port redirection all help to enable the seamless user experience. |
|
|
Local drive mapping can be done via explorer or via a command prompt. |
|
|
If you use Explorer, you map the local client drive to what is shown in the map network drive dialog. |
|
|
If you use the command prompt, the syntax is net use x \\client\y: where x is a server drive and y: is a client drive. |
|
|
Local printer mapping can be done via the Printers folder or via a command prompt. |
|
|
From the printers folder, select new printer, network printer, then select the workstation and printer (printer needs to be shared). |
|
|
From a command prompt, the syntax is net use lptx: \\client\lpty: where x is an available server printer port and y is the client port that the printer is connected to. |
|
|
Ability to make use of both the local client clipboard and server clipboard for copying/pasting data between local and server based applications. |
|
|
Enabled by default for all transport protocols; can be disabled in the CCC utility. |
|
|
Enabled by default for all protocols. Allows for listening to WAV, system and broadcast sounds if the client has a SoundBlaster-compatible sound card. |
|
|
The ICA client for DOS, Win16 or Win32 can use audio mapping. That is, WAV files in 8 or 16 bits can be played. |
|
|
High (1.3Mps), medium (64Kps) and low (16kps) quality audio can be configured for a given connection type. Audio quality can be set in the Published Application Manager (PAM) on an application set level and in the CCC utility for all applications over a given connection type. |
|
|
If audio quality levels differ from the published application to the connection, the lower setting will be selected. Only the client can adjust volume. |
|
|
Feature only of the Win32 client. |
|
|
Allows user to run multiple applications from a single ICA connection. |
|
|
Eliminates the need for users to log on each time they start another application. |
|
|
Reduces the overhead on servers by reducing the number of ICA connections. |
|
|
Applications must be set up with these components exactly the same: encryption, bitmap cache, compression, mouse/keyboard queue, audio and window colors. Else, another ICA license will be used. |
|
|
Bitmap cache settings can only be administered for application sets as a whole, not for single applications. |
|
|
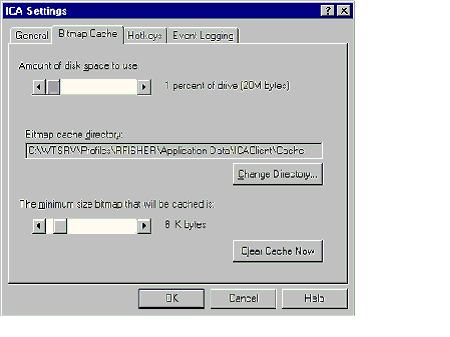
The Program Neighborhood ICA settings Bitmap Cache tab allows you to specify maximum % of hard disk space to use; it defaults to 1% of partition containing the cache directory. |
|
|
Cache directory, minimum sized bitmap cached and clear cache now options are available on the client. |
|
|
Cache info for a connection can be viewed in Citrix Server Administration via the Cache tab. |
|
|
Reduces transmission of frequently painted screens, reducing network traffic by transmitting only images that change. |
|
|
Speedscreen 1 in MF 1.0 reduced retransmission 25 to 30%. Speedscreen2 in MF1.8 reduced by up to 60%. |
|
|
Automatically configured for each ICA connection type. |
|
|
Remote Application Manager (RAM) client software provides TAPI emulation support for DOS and Win16 clients. |
|
|
Set up a Dial-in connection and the RAM will detect previously configured TAPI compliant modems or allow you to set up such modems. |
|
|
The CSA utility allows you to log off users, reset sessions, send messages, disconnect users, view/terminate processes, display client settings, connection status and shadow. |
|
|
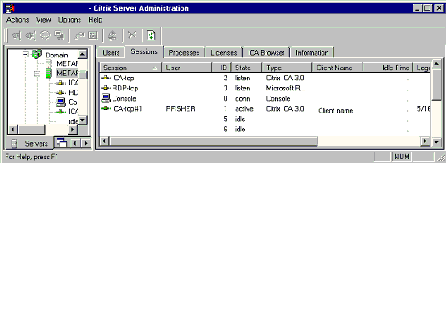
Keep in mind what tabs are available for selected views. With a server selected in the left pane as shown below, note the available tabs. With a single connection selected in the left pane, only Processes, Information, Modules and Cache tabs are available. |
|
|
CSA allows you to manage connections based on servers, published applications and video servers. The status of connections viewed from the Sessions tab can be active, listen, down, conn and idle. |
|
|
Resetting of a listener port (all configured connection types have a listener port) for a connection will reset ALL sessions over that connection. |
|
|
The two default idle connections consume 2M total server memory. |
|
|
Use the CSA utility to configure ICA gateways for server and client connectivity across subnets. |
|
|
In CSA, select all servers in the left pane then select the ICA Gateways tab in the right pane. You need to configure at least one server for an ICA gateway. |
|
|
ICA gateways are primarily intended for server-to-server communication across subnets. |
|
|
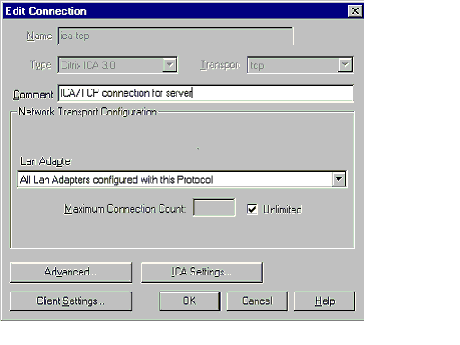
The CCC utility allows for configuration of each connection type. ICA-TCP, RDP-TCP, ICA-IPX, Async, etc. |
|
|
Manage security for each connection type. The figure below shows the configuration dialog for an ICA-TCP connection. Settings such as idle timeout, disconnect timeout, printer connections, client drive mapping, and shadow settings can be configured for ALL sessions over a given connection. As mentioned previously, audio quality is also set here for a given connection type. |
|
|
The PAM utility is a very powerful tool for setting up and managing published applications, load-balanced applications, and server farms. |
|
|
From the Application menu, you can create/manage published application(s), either load balanced or not. You can enable or disable applications, create ICA and HTML files for published application ALE use, and migrate applications to farm scope (if they were created in at least MF 1.8 domain scope). |
|
|
From the View menu, you can select server(s) to manage and change scopes. |
|
|
From the Configure menu you can create/manage server farms, migrate servers to farms or move them from farm to farm. |
|
|
In PAM, select new from the Application menu or right-click on the screen. |
|
|
Name the application as it will appear in the program neighborhood client and in PAM. |
|
|
Define whether the application is explicit (requires user authentication) or anonymous. |
|
|
Metaframe 1.8 automatically creates 15 anonymous local user accounts during initial setup. |
|
|
Define the command line, working directories (leave them blank to publish the server desktop), and default window properties. You then define domain global group and/or domain user access and server(s) to run the application on. |
|
|
The application is considered load balanced if more than one server is selected. |
|
|
If configuring in a farm scope, you can manage audio/video settings, application sets and folders for use by program neighborhood clients. |
|
|
The load balancing option pack license must be installed on each server. |
|
|
In PAM for each application, you specify each server that the application will run on. |
|
|
Application software must be installed on each load-balanced server. |
|
|
The ICA master browser (configured in the CSA utility) is the component that manages load balancing for all server connections. |
|
|
A master browser election can occur for these reasons: a server starts up, a master browser fails to respond to a request, or a master browser shuts down. |
|
|
The server with the highest ICA browser version number will always win an election regardless of settings. |
|
|
The Load Balancing Administration tool allows you to set up load balancing in a basic or advanced manner. |
|
|
Load-balancing parameters are set up on a server-by-server basis. Basic load balancing is based only on user load. |
|
|
Each server defaults to a baseline of 10000 allowable user connections. Vary this number up or down with respect to all other servers. One server set to 10000 and the other set to 11000 will place greater user load on the latter server by about 10%. |
|
|
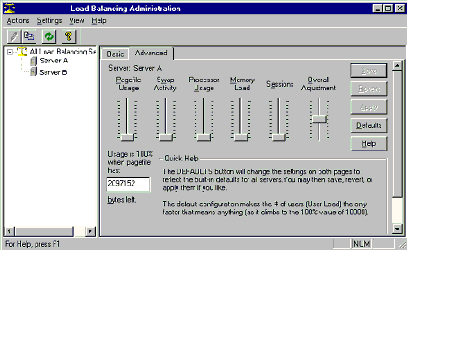
Advanced load balancing can make use of local system resource usage as shown in the figure below. Pagefile usage, swap activity, processor usage, memory load, # of open sessions relative to available sessions or overall adjustment. |
|
|
Overall adjustment is used to vary all parameters relative to each other. You can temporarily prevent a server from participating in load balancing by setting pagefile usage, swap, processor and memory to 0, and overall importance to -10. |
|
|
Server farms are created and managed in the PAM utility. |
|
|
Server farms DO NOT require a load balancing license. |
|
|
Server farms must have Administrators with administrator rights to all servers, common base of user accounts and a physical connection. |
|
|
A common base of user accounts is based on NT domain trust relationships. The domain(s) that is trusted will contain the common base of users accounts that applications can be published to. |
|
|
The physical connection can be LAN, WAN, or dial-up. An ICA gateway must be in place if servers are separated by a router. |
|
|
PAM allows you to migrate applications published in a domain scope to a farm scope if they were published in Metaframe 1.8. |
|
|
Metaframe 1.0 applications cannot be migrated. The server(s) containing the applications to be migrated must already be a member of the farm. |
|
|
Servers can be moved from one farm to another farm or to a new farm. |
|
|
Servers cannot be removed from a farm and put back in a domain scope. |
|
|
Any load-balanced applications on the server must have the server removed before taking the server out of the farm. |
|
|
Launched applications launch from an embedded ICA file in a Web page and run in a separate window. Closing the Web browser will not close the application. |
|
|
Embedded applications also launch from an ICA file embedded in a Web page, but they run inside the browser window. Closing the Web browser will close the application. |
|
|
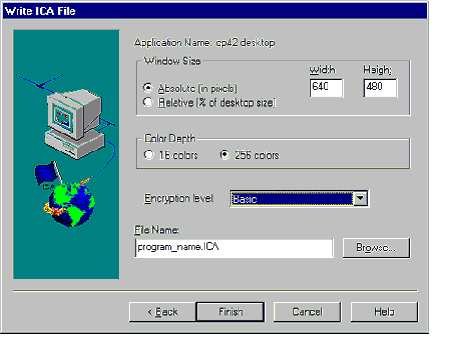
ICA files (plain text) files are created in the PAM utility. |
|
|
The published application must be created prior to creating the file. |
|
|
Using the menu or right clicking on a published application will start the ICA wizard. |
|
|
First, choose how much help you need (a little or a lot). Enter the window size in pixels or % desktop. Enter the color depth (16 or 256 colors). Enter the encryption level (defaults to basic). Finally, enter a filename and location and click Finish to create the file. |
|
|
Files default to creating in %systemroot%\system32. |
|
|
ICA files contain all the information necessary to establish communication with the server(s), what published application to launch, whether to embed or launch, and what window and color depths to use. |
|
|
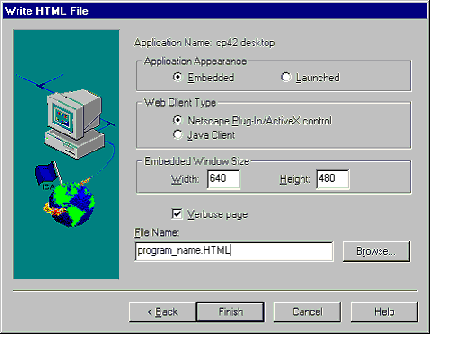
The PAM utility is also used to create HTML files from ICA files. |
|
|
Again, right click on a published application or use the menu to start HTML generation. |
|
|
Again, choose how much help you need. Select an existing ICA file or create one. |
|
|
Choose whether the application should be embedded or launched. For embedded apps, choose the type of Web client (IE/Netscape or Java) and the embedded window size. |
|
|
For embedded and launched apps, select verbose page or not, and the name of the file. Files default to creating in %systemroot%\system32. |
|
|
The HTML page is intended to house the ICA file(s) for ALE. It is not necessary to create the HTML page with this tool; it is provided more as a convenience. |
|
|
WFICA32.EXE and WFICA16.EXE are the Web plugins for Win32 and Win16 respectively. |
|
|
Simply execute wfplug32.exe or wfplug16.exe on the client and it will extract the necessary 3 files (wfica32.exe, wfica.ocx, wfica.inf); no further configuration is required. |
|
|
Java clients run in Application mode or in Applet mode. |
|
|
Application mode requires that the JVM 1.1 or higher be installed on the client. |
|
|
Applet mode runs almost entirely on the server with Web server housing java applets. |
|
|
Code is downloaded to the client each time an app is run. The Web browser must be JDK 1.1 compliant. |
|
|
TSE adds the session and user objects to Performance Monitor objects in addition to the objects supplied from regular NT server. |
|
|
The user object allows monitoring of typical counters (%proc time) against one or multiple users. |
|
|
The session object allows for monitoring of a much wider array of TSE specific counters (bitmap reads) against one or multiple sessions. |
|
|
The Data Collection Service runs on all servers to be monitored. This service monitors application and users on each server while using less than 1% of local system CPU. |
|
|
The Data Source utilizes an ODBC-compliant database or file to store information gathered by the data collection service. Excel or text files are not compliant with RMS. |
|
|
The Analysis Tools allow for the display and interpretation of data gathered by RMS. Displays are available for applications, users, fees, cost center, reports, system snapshots and current system status. |
![]()
This information came actually came from http://cramsession.brainbuzz.com/cramsession/Citrix/cca/guide.asp and NOT http://www.ais.ualberta.ca/Technical/Citrix/CitrixInstall.htm as previously stated. I apologize for the incorrect link. If this page is missing, it is because a member of brainbuzz emailed us on a holiday and cc'ed the abuse team at terrashare.com (whom is going to be shutting down (that's what you get for not listening to your customers (hahahahahahaahahahahahaha). Oh, and have a nice day)). As you know, most of these abuse teams just delete the site without reading the requests sent to them.
Please note: just a friendly reminder, any page within this help site is for MY benefit, NOT yours. I receive no money and no help from you or anyone else. Also, I am not responsible for what you do with information found here or the fact that you found it. I have no control over your actions. Act responsibly and friendly. If there you have a problem with a page (anywhere on the net), give the contact person 24 to 48 hours for them to comply with your request before you go above them (this means not cc'ing an abuse team or a persons' employer). Let's keep the net friendly and not spiteful; intentions good. When one loses, we all lose. Have a nice day.
![]()
Return to previous menu