

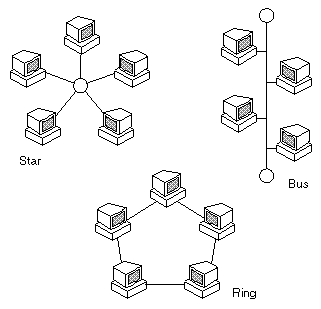
A network in which all nodes are connected to a single wire (the bus) that has two endpoints. Ethernet 10Base-2 and 10Base-5 networks, for example, are bus networks. Other common network types include star networks and ring networks. |

| collapsed backbone |
| Last modified: March 3, 2000 |
From the ports of the single switch, cables connect to the hubs of individual LAN segments.
Collapsed backbones are typically used for mid-sized LAN networks. The architecture is easier to manage and easier to keep secure, not to mention less costly.

| EtherLoop |
| Last modified: April 19, 2000 |
Similar to Ethernet, Etherloop transmits data packets in bursts. Between bursts, EtherLoop looks for problems and interference in the lines and knows to steer clear and find an alternate path. Also, EtherLoop is Ethernet compliant, so it is easily adaptable to existing Ethernet systems.
EtherLoop also borrows from the best of DSL to offer point-to-point security and a non-shared medium (more users don't slow down connection speed), But unlike DSL, EtherLoop avoids impacting other services such as ISDN, T-1, ADSL, HDSL and SDSL, which are in the same cable binder group.
EtherLoop is not proprietary. Elastic Networks plans on licensing the technology to manufacturers who can design and create their own EtherLoop solutions.

| MAC Layer |
| Last modified: November 9, 1999 |
The MAC sublayer uses MAC protocols to ensure that signals sent from different stations across the same channel don't collide.
Different protocols are used for different shared networks, such as Ethernets, Token Rings, Token Buses, and WANs.

| mesh |
| Last modified: August 26, 1999 |
There are two types of mesh topologies: full mesh and partial mesh.
Full mesh topology occurs when every node has a circuit connecting it to every other node in a network. Full mesh is very expensive to implement but yields the greatest amount of redundancy, so in the event that one of those nodes fails, network traffic can be directed to any of the other nodes. Full mesh is usually reserved for backbone networks.
Partial mesh topology is less expensive to implement and yields less redundancy than full mesh topology. With partial mesh, some nodes are organized in a full mesh scheme but others are only connected to one or two in the network. Partial mesh topology is commonly found in peripheral networks connected to a full meshed backbone.

| ring network |
| Last modified: September 1, 1996 |

| star network |
| Last modified: May 19, 1998 |
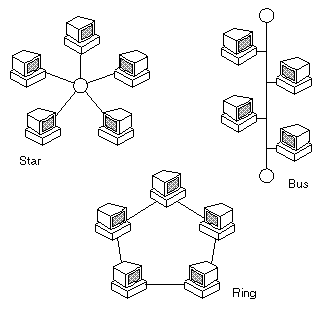
A local-area network (LAN) that uses a star topology in which all nodes are connected to a central computer. The main advantages of a star network is that one malfunctioning node doesn't affect the rest of the network, and it's easy to add and remove nodes. The main disadvantage of star networks is that they require more cabling than other topologies, such as a bus or ring networks. In addition, if the central computer fails, the entire network becomes unusable.
Standard twisted-pair Ethernet uses a star topology.

| token bus network |
| Last modified: October 30, 1997 |

| token-ring network |
| Last modified: November 4, 1997 |
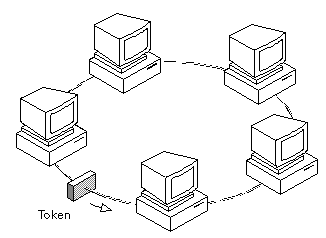
(1) A type of computer network in which all the computers are arranged (schematically) in a circle. A token, which is a special bit pattern, travels around the circle. To send a message, a computer catches the token, attaches a message to it, and then lets it continue to travel around the network.
(2) When capitalized, Token Ring refers to the PC network protocol developed by IBM. The IBM Token-Ring specification has been standardized by the IEEE as the IEEE 802.5 standard.

| topology (summary) |
| Last modified: May 19, 1998 |
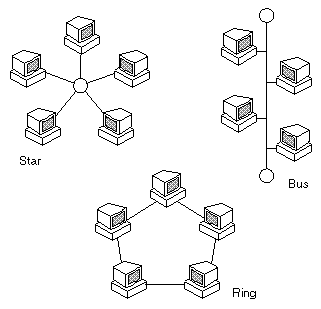
The shape of a local-area network (LAN) or other communications system. There are three principal topologies used in LANs.
|
|
bus topology: All devices are connected to a central cable, called the bus or backbone. Bus networks are relatively inexpensive and easy to install for small networks. Ethernet systems use a bus topology. |
|
|
ring topology : All devices are connected to one another in the shape of a closed loop, so that each device is connected directly to two other devices, one on either side of it. Ring topologies are relatively expensive and difficult to install, but they offer high bandwidth and can span large distances. |
|
|
star topology: All devices are connected to a central hub. Star networks are relatively easy to install and manage, but bottlenecks can occur because all data must pass through the hub. |
These topologies can also be mixed. For example, a bus-star network consists of a high-bandwidth bus, called the backbone, which connects a collections of slower-bandwidth star segments.

| architecture |
| Last modified: September 1, 1997 |
An open architecture allows the system to be connected easily to devices and programs made by other manufacturers. Open architectures use off-the-shelf components and conform to approved standards. A system with a closed architecture, on the other hand, is one whose design is proprietary, making it difficult to connect the system to other systems.

| ATM |
| Last modified: November 4, 1997 |
Current implementations of ATM support data transfer rates of from 25 to 622 Mbps (megabits per second). This compares to a maximum of 100 Mbps for Ethernet, the current technology used for most LANs.
Some people think that ATM holds the answer to the Internet bandwidth problem, but others are skeptical. ATM creates a fixed channel, or route, between two points whenever data transfer begins. This differs from TCP/IP, in which messages are divided into packets and each packet can take a different route from source to destination. This difference makes it easier to track and bill data usage across an ATM network, but it makes it less adaptable to sudden surges in network traffic.
When purchasing ATM service, you generally have a choice of four different types of service:
|
|
Constant Bit Rate (CBR) specifies a fixed bit rate so that data is sent in a steady stream. This is analogous to a leased line. |
|
|
Variable Bit Rate (VBR) provides a specified throughput capacity but data is not sent evenly. This is a popular choice for voice and videoconferencing data. |
|
|
Unspecified Bit Rate (UBR) does not guarantee any throughput levels. This is used for applications, such as file transfer, that can tolerate delays. |
|
|
Available Bit Rate (ABR) provides a guaranteed minimum capacity but allows data to be bursted at higher capacities when the network is free. |

| bandwidth |
| Last modified: May 14, 1998 |
The bandwidth is particularly important for I/O devices. For example, a fast disk drive can be hampered by a bus with a low bandwidth. This is the main reason that new buses, such as AGP, have been developed for the PC.

(2) For IBM PS/2 computers, a channel is the same as an expansion bus. |

| circuit switching |
| Last modified: September 1, 1997 |
The other common communications method is packet switching, which divides messages into packets and sends each packet individually. The packets may take different routes and may arrive out of order. The Internet is based on a packet-switching protocol, TCP/IP.
Circuit-switching systems are ideal for communications that require data to be transmitted in real-time. Packet-switching networks are more efficient if some amount of delay is acceptable.
Circuit-switching networks are sometimes called connection-oriented networks. Note, however, that although packet switching is essentially connectionless, a packet switching network can be made connection-oriented by using a higher-level protocol. TCP, for example, makes IP networks connection-oriented.

| client/server architecture |
| Last modified: December 22, 1997 |
Another type of network architecture is known as a peer-to-peer architecture because each node has equivalent responsibilities. Both client/server and peer-to-peer architectures are widely used, and each has unique advantages and disadvantages.
Client-server architectures are sometimes called two-tier architectures, refers to client/server architectures in which the user interface runs on the client and the database is stored on the server. The actual application logic can run on either the client or the server. A newer client/server architecture, called a three-tier architecture introduces a middle tier for the application logic.

| connectionless |
| Last modified: May 1, 1997 |
In contrast, connection-oriented protocols require a channel to be established between the sender and receiver before any messages are transmitted. Examples of connection-oriented protocols include the telephone, TCP, and HTTP.

| coaxial cable |
| Last modified: September 1, 1997 |
A type of wire that consists of a center wire surrounded by insulation and then a grounded shield of braided wire. The shield minimizes electrical and radio frequency interference.
Coaxial cabling is the primary type of cabling used by the cable television industry and is also widely used for computer networks. Although more expensive than standard telephone wire, it is much less susceptible to interference and can carry much more data. Because the cable television industry has already connected millions of homes with coaxial cable, many analysts believe that they are the best positioned to capitalize on the much-heralded information highway.

| CSMA/CD |
| Last modified: June 1, 1999 |
CSMA/CD is a type of contention protocol. A type of network protocol that allows nodes to contend for network access. That is, two or more nodes may try to send messages across the network simultaneously. The contention protocol defines what happens when this occurs

| data compression |
| Last modified: May 14, 1998 |
Data compression is particularly useful in communications because it enables devices to transmit the same amount of data in fewer bits. There are a variety of data compression techniques, but only a few have been standardized. The CCITT has defined a standard data compression technique for transmitting faxes (Group 3 standard) and a compression standard for data communications through modems (CCITT V.42bis). In addition, there are file compression formats, such as ARC and ZIP.
Data compression is also widely used in backup utilities, spreadsheet applications, and database management systems. Certain types of data, such as bit-mapped graphics, can be compressed to a small fraction of their normal size.

| dial-up access |
| Last modified: May 11, 1999 |
An alternative way to connect two computers is through a leased line, which is a permanent connection between two devices. Leased lines provide faster throughput and better quality connections, but they are also more expensive.

| DLC |
| Last modified: October 14, 1997 |
For networks that conform to the IEEE 802 standards (e.g., Ethernet ), the DLC address is usually called the Media Access Control (MAC) address.
| Layer | Name | Function |
| 7 | Application Layer | Program-to-program communication. |
| 6 | Presentation Layer | Manages data representation conversions. For example, the Presentation Layer would be responsible for converting from EBCDIC to ASCII. |
| 5 | Session Layer | Responsible for establishing and maintaining communications channels. In practice, this layer is often combined with the Transport Layer. |
| 4 | Transport Layer | Responsible for end-to-end integrity of data transmission. |
| 3 | Network Layer | Routes data from one node to another. |
| 2 | Data Link Layer | Responsible for physical passing data from one node to another. |
| 1 | Physical Layer | Manages putting data onto the network media and taking the data off. |

| Ethernet |
| Last modified: May 15, 1998 |
A newer version of Ethernet, called 100Base-T (or Fast Ethernet), supports data transfer rates of 100 Mbps. And the newest version, Gigabit Ethernet supports data rates of 1 gigabit (1,000 megabits) per second.

| FDM |
| Last modified: July 1, 1997 |

| fiber optics |
| Last modified: April 29, 1998 |
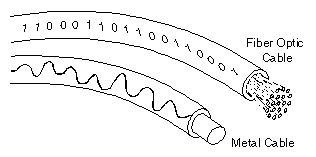
A technology that uses glass (or plastic) threads (fibers) to transmit data. A fiber optic cable consists of a bundle of glass threads, each of which is capable of transmitting messages modulated onto light waves.
Fiber optics has several advantages over traditional metal communications lines:
|
|
Fiber optic cables have a much greater bandwidth than metal cables. This means that they can carry more data. |
|
|
Fiber optic cables are less susceptible than metal cables to interference. |
|
|
Fiber optic cables are much thinner and lighter than metal wires. |
|
|
Data can be transmitted digitally (the natural form for computer data) rather than analogically. |
The main disadvantage of fiber optics is that the cables are expensive to install. In addition, they are more fragile than wire and are difficult to split.
Fiber optics is a particularly popular technology for local-area networks. In addition, telephone companies are steadily replacing traditional telephone lines with fiber optic cables. In the future, almost all communications will employ fiber optics.

| Frame Relay |
| Last modified: November 17, 1997 |
In the U.S., Frame Relay is quite popular because it is relatively inexpensive. However, it is being replaced in some areas by faster technologies, such as ATM.

| hub |
| Last modified: December 8, 1997 |
A passive hub serves simply as a conduit for the data, enabling it to go from one device (or segment) to another. So-called intelligent hubs include additional features that enables an administrator to monitor the traffic passing through the hub and to configure each port in the hub. Intelligent hubs are also called manageable hubs.
A third type of hub, called a switching hub, actually reads the destination address of each packet and then forwards the packet to the correct port.

|

| IEEE 802 standards |
| Last modified: November 25, 1997 |
|
|
IEEE 802.1: Standards related to network management. |
|
|
IEEE 802.2: General standard for the data link layer in the OSI Reference Model. The IEEE divides this layer into two sublayers -- the data link control (DLC) layer and the media access control (MAC) layer. The MAC layer varies for different network types and is defined by standards IEEE 802.3 through IEEE 802.5. |
|
|
IEEE 802.3: Defines the MAC layer for bus networks that use CSMA/CD. This is the basis of the Ethernet standard. |
|
|
IEEE 802.4: Defines the MAC layer for bus networks that use a token-passing mechanism (token bus networks). |
|
|
IEEE 802.5: Defines the MAC layer for token-ring networks. |
|
|
IEEE 802.6: Standard for Metropolitan Area Networks (MANs). |

| ISO |
| Last modified: May 16, 1998 |

| ITU |
| Last modified: March 11, 1997 |
|
Protocol |
Maximum Transmission Rate |
Duplex Mode |
| Bell 103 | 300 bps | Full |
| CCITT V.21 | 300 bps | Full |
| Bell 212A | 1,200 bps | Full |
| ITU V.22 | 1,200 bps | Half |
| ITU V.22bis | 2,400 bps | Full |
| ITU V.29 | 9,600 bps | Half |
| ITU V.32 | 9,600 bps | Full |
| ITU V.32bis | 14,400 bps | Full |
| ITU V.34 | 36,600 bps | Full |
| ITU V.90 | 56,000 bps | Full |

| leased line |
| Last modified: February 26, 1998 |
For example, a T-1 channel is a type of leased line that provides a maximum transmission speed of 1.544 Mbps. You can divide the connection into different lines for data and voice communication or use the channel for one high speed data circuit. Dividing the connection is called multiplexing.
Increasingly, leased lines are being used by companies, and even individuals, for Internet access because they afford faster data transfer rates and are cost-effective if the Internet is used heavily.

| local-area network |
| Last modified: May 16, 1998 |
Most LANs connect workstations and personal computers. Each node (individual computer ) in a LAN has its own CPU with which it executes programs, but it is also able to access data and devices anywhere on the LAN. This means that many users can share expensive devices, such as laser printers, as well as data. Users can also use the LAN to communicate with each other, by sending e-mail or engaging in chat sessions.
There are many different types of LANs Ethernets being the most common for PCs. Most Apple Macintosh networks are based on Apple's AppleTalk network system, which is built into Macintosh computers.
The following characteristics differentiate one LAN from another:
|
|
topology : The geometric arrangement of devices on the network. For example, devices can be arranged in a ring or in a straight line. |
|
|
protocols : The rules and encoding specifications for sending data. The protocols also determine whether the network uses a peer-to-peer or client/server architecture. |
|
|
media : Devices can be connected by twisted-pair wire, coaxial cables, or fiber optic cables. Some networks do without connecting media altogether, communicating instead via radio waves. |
LANs are capable of transmitting data at very fast rates, much faster than data can be transmitted over a telephone line; but the distances are limited, and there is also a limit on the number of computers that can be attached to a single LAN.

On networks that do not conform to the IEEE 802 standards but do conform to the OSI Reference Model, the node address is called the Data Link Control (DLC) address. |

| media |
| Last modified: October 5, 1997 |
(2) In computer networks, media refers to the cables linking workstations together. There are many different types of transmission media, the most popular being twisted-pair wire (normal electrical wire), coaxial cable (the type of cable used for cable television), and fiber optic cable (cables made out of glass).
(3) The form and technology used to communicate information. Multimedia presentations, for example, combine sound, pictures, and videos, all of which are different types of media.

| multiplex |
| Last modified: November 10, 1997 |
|
|
Frequency Division Multiplexing (FDM) : each signal is assigned a different frequency |
|
|
Time Division Multiplexing (TDM) : each signal is assigned a fixed time slot in a fixed rotation |
|
|
Statistical Time Division Multiplexing (STDM): time slots are assigned to signals dynamically to make better use of bandwidth |
|
|
Wavelength Division Multiplexing (WDM) : each signal is assigned a particular wavelength; used on optical fiber. |

| network |
| Last modified: September 1, 1996 |

A group of two or more computer systems linked together. There are many types of computer networks, including:
|
|
local-area networks (LANs) : The computers are geographically close together (that is, in the same building). |
|
|
wide-area networks (WANs) : The computers are farther apart and are connected by telephone lines or radio waves. |
In addition to these types, the following characteristics are also used to categorize different types of networks:
|
|
topology : The geometric arrangement of a computer system. Common topologies include a bus, star, and ring. |
|
|
protocol : The protocol defines a common set of rules and signals that computers on the network use to communicate. One of the most popular protocols for LANs is called Ethernet. Another popular LAN protocol for PCs is the IBM token-ring network . |
|
|
architecture : Networks can be broadly classified as using either a peer-to-peer or client/server architecture. |
Computers on a network are sometimes called nodes. Computers and devices that allocate resources for a network are called servers.

|

| OSI |
| Last modified: May 16, 1998 |
Short for Open System Interconnection, an ISO standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. Control is passed from one layer to the next, starting at the application layer in one station, proceeding to the bottom layer, over the channel to the next station and back up the hierarchy.
At one time, most vendors agreed to support OSI in one form or another, but OSI was too loosely defined and proprietary standards were too entrenched. Except for the OSI-compliant X.400 and X.500 e-mail and directory standards, which are widely used, what was once thought to become the universal communications standard now serves as the teaching model for all other protocols.
Most of the functionality in the OSI model exists in all communications systems, although two or three OSI layers may be incorporated into one.
OSI is also referred to as the OSI Reference Model or just the OSI Model.

Most modern Wide Area Network (WAN) protocols, including TCP/IP, X.25, and Frame Relay, are based on packet-switching technologies. In contrast, normal telephone service is based on a circuit-switching technology, in which a dedicated line is allocated for transmission between two parties. Circuit-switching is ideal when data must be transmitted quickly and must arrive in the same order in which it's sent. This is the case with most real-time data, such as live audio and video. Packet switching is more efficient and robust for data that can withstand some delays in transmission, such as e-mail messages and Web pages. A new technology, ATM, attempts to combine the best of both worlds -- the guaranteed delivery of circuit-switched networks and the robustness and efficiency of packet-switching networks. |

PCM is used with T-1 and T-3 carrier systems. These carrier systems combine the PCM signals from many lines and transmit them over a single cable or other medium. |

| peer-to-peer architecture |
| Last modified: May 18, 1998 |

| protocol |
| Last modified: September 1, 1996 |
|
|
the type of error checking to be used |
|
|
data compression method, if any |
|
|
how the sending device will indicate that it has finished sending a message |
|
|
how the receiving device will indicate that it has received a message |
There are a variety of standard protocols from which programmers can choose. Each has particular advantages and disadvantages; for example, some are simpler than others, some are more reliable, and some are faster.
From a user's point of view, the only interesting aspect about protocols is that your computer or device must support the right ones if you want to communicate with other computers. The protocol can be implemented either in hardware or in software.

| switch |
| Last modified: March 22, 1998 |

|

| throughput |
| Last modified: May 18, 1998 |

| twisted-pair cable |
| Last modified: September 1, 1996 |

| WDM |
| Last modified: October 12, 1999 |

| wide-area network |
| Last modified: August 12, 1997 |
Computers connected to a wide-area network are often connected through public networks, such as the telephone system. They can also be connected through leased lines or satellites. The largest WAN in existence is the Internet.

| X.25 |
| Last modified: August 11, 1997 |

| X.400 |
| Last modified: August 24, 1997 |

| X.500 |
| Last modified: August 24, 1997 |

This information came from http://webopedia.internet.com
Return to previous menu